An AWS Lambda function can run a command on your computer
-
AWS Lambda functions are very cheap and easy to use. They take a json object called an "event" as input, and return a json object. They can run a few different languages including Python. The example below is Python, but I'm willing to do a Node.JS version if someone wants me to.
I used the Oregon / us-west-2 region for this. If you pick a different region, just update that in the code.
This Lambda function expects an input event with this format:
{ "trigger": "notepad", "computer": "laptop", "params": "your optional command parameters" }To avoid storing your token in your Lambda function, create a secret called triggercmd_token in AWS Secrets Manager with these contents:
{ "token": "(your token from the Instructions page)" }Create a Python3 Lambda with these contents:
import json, urllib3, boto3 from botocore.exceptions import ClientError def lambda_handler(event, context): print(json.dumps(event)) trigger = event['trigger'] computer = event['computer'] secret = get_secret('triggercmd_token') token = secret['token'] url = 'https://www.triggercmd.com/api/run/triggerSave?computer=' + computer + '&trigger=' + trigger + '&token=' + token if 'params' in event: params = event['params'] url = url + '¶ms=' + params http = urllib3.PoolManager() r = http.request('GET', url) r.status if r.status == 200: return { 'statusCode': 200, 'body': r.data.decode('utf-8') } else: return { 'statusCode': 404, 'body': json.dumps('Something went wrong.') } def get_secret(secret_name): region_name = "us-west-2" session = boto3.session.Session() client = session.client( service_name='secretsmanager', region_name=region_name, ) try: get_secret_value_response = client.get_secret_value( SecretId=secret_name ) except ClientError as e: print(e) else: text_secret_data = get_secret_value_response['SecretString'] return json.loads(text_secret_data)Last step - to give your Lambda access to your triggercmd_token secret:
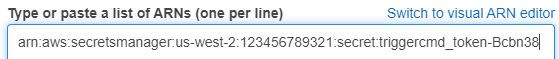
Copy your triggercmd_token secret's ARN, which looks like this:
arn:aws:secretsmanager:us-west-2:123456789321 triggercmd_token-Bcbn38
triggercmd_token-Bcbn38In your Lambda's permissions tab, click the role, click the policy, click Edit policy, click Add additional permissions.
For the service, choose Secrets Manager, click Read, click Resources, click Add ARN, click List ARNs manually, and paste in your ARN like this:
Click Add, Review policy, and Save changes.Now you're ready to click the Test button to test your Lambda.